Introduction to road map for a vulnerability management team medium
In today’s fast-paced digital landscape, organizations face an ever-growing array of cybersecurity threats. With these challenges comes the critical need for a robust vulnerability management team—a group dedicated to identifying, assessing, and mitigating risks that could compromise sensitive data. But how do you build an road map for a vulnerability management team medium? A well-structured road map is essential to navigate this complex field. This guide will walk you through the key elements needed for creating a successful roadmap tailored specifically for your organization’s needs. Whether you’re starting from scratch or looking to enhance your current processes, understanding what it takes to develop a solid framework can make all the difference in keeping your organization secure. Let’s dive into the essentials of developing a strategic approach that empowers your vulnerability management team and fortifies your defenses against potential attacks.
The Importance of a Vulnerability Management Team
A vulnerability management team plays a critical role in any organization’s cybersecurity strategy. They are the frontline defenders against potential threats that could exploit weaknesses in systems and applications.
With cyberattacks on the rise, having dedicated professionals who can identify, assess, and prioritize vulnerabilities is essential. This proactive approach protects sensitive data and ensures regulatory compliance.
Moreover, these teams foster a culture of security awareness across all departments. By collaborating with IT staff and other stakeholders, they ensure that security measures align with business objectives.
Their efforts not only mitigate risks but also bolster trust among clients and partners. A strong vulnerability management framework instills confidence that an organization takes its cybersecurity seriously.
Roles and Responsibilities of a Vulnerability Management Team
A vulnerability management team plays a critical role in safeguarding an organization’s digital assets. Each member contributes specific skills that enhance the team’s overall effectiveness.
First, there are analysts who specialize in identifying vulnerabilities through various tools and techniques. They continuously monitor systems to discover potential weaknesses before they can be exploited.
Then, risk assessors focus on evaluating the impact of identified vulnerabilities. Their analyses help prioritize which issues need immediate attention based on potential risks to the organization.
Remediation experts take charge of developing strategies for fixing these vulnerabilities. Collaboration with IT teams ensures that patches or updates are implemented efficiently without disrupting operations.
Communication is vital. The team must keep stakeholders informed about ongoing threats and remediation efforts. This transparency fosters trust and encourages a collective approach to security within the organization.
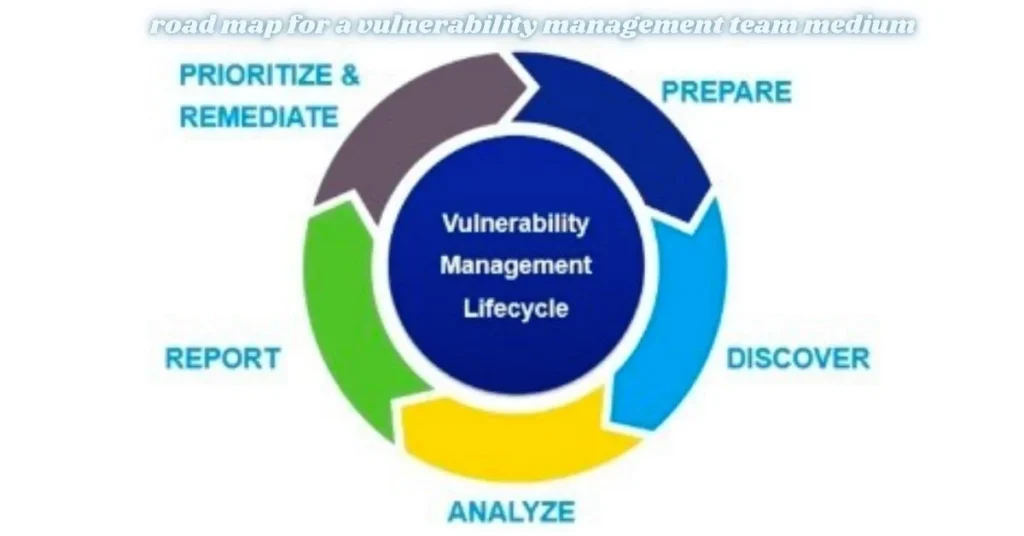
Creating a Roadmap for Your Vulnerability Management Team
Creating a roadmap for your vulnerability management team requires strategic planning and clarity. Start by defining the team’s objectives, aligning them with your organization’s overall security goals.
Next, outline key milestones that reflect the different phases of vulnerability management. This could include risk assessment timelines, remediation deadlines, and scheduled audits.
Engage team members in discussions about their priorities and challenges. Their insights will enrich the roadmap and ensure everyone is on board.
Incorporate flexible elements to adapt to evolving threats. Cybersecurity landscapes change rapidly; your plan should be able to pivot when new vulnerabilities emerge.
Visualize this roadmap using charts or diagrams for easy reference. A clear visual representation can enhance understanding across departments and facilitate smoother execution of tasks.
Identifying Vulnerabilities and Assessing Risk
Identifying vulnerabilities is the first step in a robust vulnerability management strategy. This process involves scanning systems, applications, and networks for weaknesses that could be exploited by attackers. Regular scans help ensure no stone is left unturned.
Once vulnerabilities are identified, assessing their risk becomes crucial. Not all weaknesses carry the same potential impact. A thorough assessment considers factors like exploitability, affected assets, and possible damage.
Employing risk scoring frameworks can simplify this task. These frameworks prioritize vulnerabilities based on severity and business context. Teams can then focus on what truly matters.
Involving stakeholders from various departments also enhances understanding of risks associated with specific assets or processes. Collaboration fosters a comprehensive view of what needs immediate attention versus those that may pose lower threats over time.
Prioritizing and Remediating Vulnerabilities
Prioritizing vulnerabilities is essential for effective risk management. Not all vulnerabilities pose the same level of threat. Distinguishing between critical, high, medium, and low risks helps allocate resources efficiently.
Once you’ve identified priorities, remediation becomes the focus. Implementing fixes should be strategic and timely to minimize potential damage. Quick wins can provide immediate security boosts while longer-term solutions are developed.
Collaboration plays a vital role in this phase. Involving cross-functional teams ensures that technical issues align with business objectives. This encourages ownership across departments.
Moreover, continuous monitoring is crucial after remediation efforts are completed. New vulnerabilities can emerge as systems evolve or new technologies are adopted. A proactive approach keeps your organization resilient against evolving threats and enhances overall security posture.
Communication and Collaboration within the Team
Effective communication is the cornerstone of any successful vulnerability management team. Team members must feel empowered to share insights and observations freely, creating an environment where every voice matters.
Regular meetings foster openness. Scheduling weekly check-ins provides a platform for discussing ongoing projects and emerging threats. This synergy helps in identifying potential vulnerabilities before they escalate.
Collaboration tools play a vital role as well. Utilizing platforms that allow real-time updates keeps everyone aligned on priorities and tasks. It ensures that no one feels isolated from the decision-making process.
Encouraging cross-functional collaboration can enhance outcomes too. Engaging with IT, compliance, and operations teams broadens perspectives and drives comprehensive solutions to vulnerability issues.
Promoting a culture of shared responsibility reinforces teamwork while emphasizing that security is everyone’s concern—together, each member contributes to safeguarding the organization against potential breaches.
Measuring Success and Continuous Improvement
Measuring success in vulnerability management goes beyond just fixing issues. It requires a deep dive into metrics that showcase the effectiveness of your strategies.
Key performance indicators (KPIs) such as the number of vulnerabilities identified, time taken for remediation, and percentage of vulnerabilities closed should be monitored regularly. These metrics provide insight into how well your team is functioning.
Continuous improvement is vital. Once you gather data on these KPIs, use it to refine processes and enhance communication within the team. Regularly review what works and what doesn’t.
Feedback loops play an essential role in this journey. Encourage open discussions about challenges faced during vulnerability assessments or remediations. This fosters collaboration and innovation among team members.
Investing in training can also lead to better outcomes. Equip your team with updated knowledge on emerging threats and technologies, ensuring they remain at the forefront of vulnerability management practices.
Challenges Faced by Vulnerability Management Teams
Vulnerability management teams face a myriad of challenges that can hinder their effectiveness. One significant hurdle is the sheer volume of vulnerabilities detected daily. This constant influx can overwhelm even the most prepared teams.
Another challenge lies in prioritization. Not all vulnerabilities pose equal risk, yet deciding which ones to address first requires careful assessment and collaboration across departments.
Additionally, staying updated with evolving threats is crucial. Cybercriminals are constantly developing new tactics, making it essential for teams to adapt quickly.
Resource constraints further complicate matters. Limited budgets or staffing shortages often mean that teams must do more with less.
Fostering communication between IT and other stakeholders can be difficult but remains vital for successful vulnerability management efforts. Achieving alignment ensures everyone understands risks and plays an active role in mitigation strategies.
Conclusion: Building an road map for a vulnerability management team medium
Building a robust road map for a vulnerability management team medium is essential in today’s ever-evolving digital landscape. The foundation laid by understanding the importance of such teams cannot be overstated; they are critical to maintaining the integrity and security of an organization.
A well-defined roadmap encompasses clear roles and responsibilities, ensuring every team member understands their part in mitigating risks. Identifying vulnerabilities, assessing risk levels, prioritizing remediation efforts, and fostering communication within the team all contribute to a streamlined approach that enhances efficiency.
Moreover, measuring success through key performance indicators allows teams to adapt and improve continuously. This iterative process not only strengthens defenses but also cultivates resilience against future threats.
Challenges will inevitably arise. However, embracing them as opportunities for growth can lead your vulnerability management efforts to new heights. With dedication and strategic planning, every organization has the potential to create an effective roadmap that not only protects its assets but also builds trust among stakeholders.
The journey of building this roadmap is ongoing—one that requires commitment from all members involved. As organizations continue to navigate complex cyber landscapes, having a solid framework for your vulnerability management team ensures preparedness against any security challenges ahead.
ALSO RAED: is medium a good platform for extracurricular activities
FAQs
What is “Road Map for a Vulnerability Management Team Medium”?
A strategic guide that outlines key objectives, roles, and actions for building an effective vulnerability management team.
Why is a Vulnerability Management Team important?
This team proactively identifies and mitigates risks to safeguard sensitive data, ensuring compliance and security.
How do I create a roadmap for my vulnerability management team?
Define clear objectives, set milestones, and engage the team in prioritizing actions, while allowing flexibility for evolving threats.
What roles are involved in a vulnerability management team?
Analysts, risk assessors, and remediation experts each play key roles in identifying vulnerabilities, assessing risk, and fixing issues.
How can success be measured in vulnerability management?
Track KPIs like vulnerabilities identified, remediation time, and percentage closed, using this data to continuously improve processes.